What is Passwordless Authentication? How does it work?
Why Implement Passwordless Authentication?
Passwordless authentication addresses both user satisfaction and access security:
- Improving User Satisfaction: Traditional password-based systems are often cumbersome and prone to user frustration due to forgotten passwords or password resets. Passwordless methods simplify the login process by eliminating the need for users to remember complex passwords. This reduces friction during authentication and enhances the overall user experience by providing a seamless and efficient way to access systems.
- Enhancing Access Security with MFA: Multi-factor authentication (MFA) protects your data and assets in today’s digital landscape. While MFA may seem time-consuming, its integration with passwordless authentication brings significant benefits for user satisfaction. Organizations can customize MFA requirements by offering multiple authentication factors to fit the administration preferences and operational needs. These factors include what the user knows (e.g., a PIN), possesses (e.g., a smartphone or smart card), or is (e.g., biometric data like fingerprints or facial recognition). This approach prevents data breaches and enhances security by reducing the reliance on passwords and ensuring a seamless and user-friendly authentication experience.
- Maximizing Productivity with Passwordless SSO: Passwordless single sign-on (SSO) significantly boosts productivity by simplifying the authentication process across multiple applications and services. With passwordless SSO, users authenticate once using a passwordless method and gain access to a range of applications without needing to re-enter credentials. It reduces the time and effort required for logging into different systems, minimizing interruptions and allowing users to focus on their tasks. Additionally, IT support teams experience fewer password-related issues, leading to lower support costs and more efficient use of resources. Passwordless SSO improves workflow efficiency, reduces downtime, and enhances user satisfaction, contributing to a more productive work environment.
What Are Possession Factors in Passwordless Authentication?
Possession factors are essential components of passwordless authentication, using a physical item the user possesses to verify their identity. These factors enhance security and streamline user experience by reducing reliance on traditional passwords. Key possession factors used in passwordless authentication include:
- Smartphones: Smartphones generate one-time passcodes, receive push notifications for approval on authenticator apps, or use built-in biometrics for authentication. Users can approve access requests through mobile devices, providing a seamless and secure experience.
- Smart Cards: Smart cards are physical cards with embedded integrated circuits. Users tap or insert these cards into a reader to authenticate themselves, ensuring security through the card’s physical presence.
- Hardware Tokens: Hardware tokens generate one-time passcodes that users input during the login process. These tokens are highly secure as they cannot be easily replicated or stolen digitally.
- USB Security Keys: USB security keys, such as YubiKeys, are physical devices that users insert into a computer’s USB port to authenticate. They often work alongside biometric or PIN verification for enhanced security.
Exploring Different Passwordless Authentication Methods
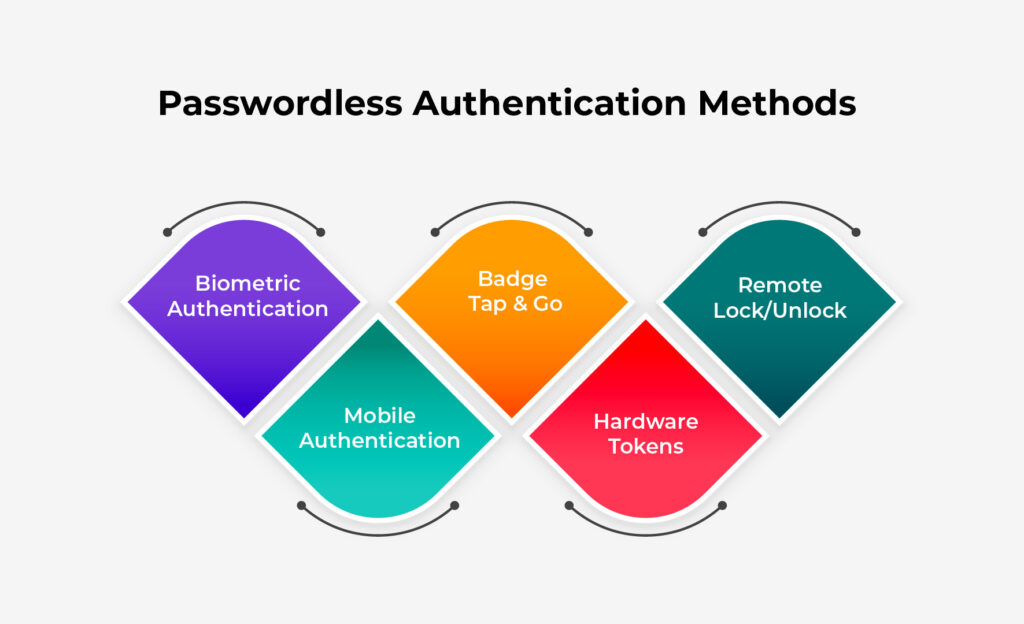
Passwordless authentication methods are gaining traction because they can enhance user experience while bolstering security. Below, we explore various passwordless authentication methods and their unique benefits.
- Biometric Authentication: Biometric authentication leverages unique biological traits such as fingerprints, facial recognition, or iris scans to verify user identity. This method offers a high level of security since these traits are difficult to replicate or forge. Users benefit from the convenience of not needing to remember or manage passwords, while organizations can reduce the risk of unauthorized access due to compromised passwords.
- Mobile Authentication: Mobile devices are everywhere and can be effectively utilized for passwordless sign in. Methods include sending a one-time passcode (OTP) via SMS, push notifications through authentication apps, or using built-in biometric sensors like fingerprint scanners or facial recognition.
- Badge Tap & Go: Badge Tap & Go authentication uses proximity cards or intelligent badges with RFID or NFC technology. Users tap their badge against a reader to gain access, simplifying the authentication process and eliminating the need for passwords.
- Hardware Tokens: Hardware tokens, such as USB keys or smart cards, provide a secure method for passwordless log in by generating time-based or event-based one-time passwords (OTPs) or through cryptographic authentication. These tokens can take various forms, ensuring secure access to systems and applications.
- Remote Lock/Unlock: Remote lock/unlock functionality allows users to secure or access their systems from a distance using their mobile device. This method enhances security by providing control over access in real-time from anywhere.
Benefits of Going Passwordless
- Convenience: Users no longer need to remember complex passwords or deal with frequent password resets.
- Speed: Authentication processes become quicker, reducing time spent logging in.
- User Satisfaction: Enhanced security and convenience lead to higher satisfaction and productivity.
- Enhanced Security: Reduces the risk of password-related breaches and phishing attacks.
- Cost Savings: Lowers the costs associated with password management, such as resets and helpdesk support.
- Regulatory Compliance: Simplifies adherence to security regulations and standards.

Transition challenges of opting for passwordless access
While passwordless authentication can present challenges, the long-term benefits outweigh the initial hurdles. Organizations must address issues such as system integration, user education, and ensuring compatibility with existing infrastructure. However, once these challenges are overcome, the benefits are substantial.
Challenges:
- Integration: Ensuring new systems work seamlessly with existing IT infrastructure.
- User Education: Training users to adopt and trust new authentication methods.
- Cost: Initial investment in new technologies and training programs.
Conclusion: Implementing Passwordless Authentication with AuthX
Implementing passwordless authentication can transform organizational security and elevate user experience. AuthX offers comprehensive features to facilitate a seamless and effective transition to passwordless access. We provide robust solutions to meet the diverse needs of modern organizations. With advanced authentication modalities such as biometric verification, mobile-based authentication, remote lock/unlock, hardware tokens, and Badge Tap & Go, AuthX ensures secure and simplified access management.
Our user-centric approach and advanced features make the transition to passwordless authentication an upgrade and a strategic advancement in digital security and operational efficiency. Embrace the future of authentication with AuthX and experience the full potential of your organization’s digital security posture. Schedule a demo with our experts to know more.















