You’re not alone if you’ve heard “FIDO” more times than “Zero Trust” this year. Whether it’s a “FIDO vs FIDO2” debate or a chart comparing FIDO U2F vs FIDO2, the buzz is real. It’s showing up in every IT security roadmap and MFA migration plan.
But here’s the thing: FIDO isn’t just another buzzword. It’s the foundation of a passwordless future, and understanding the difference between FIDO, FIDO2 vs U2F, and CTAP is more vital than it sounds, especially if you’re fielding MFA fatigue complaints or struggling with compliance.
So, let’s break it down.
What Is FIDO?
FIDO (Fast Identity Online) is a standards initiative led by the FIDO Alliance—a group of tech giants like Microsoft, Google, Apple, working together to kill the password.
We often hear: “We already have 2FA. Isn’t that enough?”
Not really. Most of today’s 2FA methods still rely on shared secrets—passwords, codes, or push approvals.
The original FIDO protocols aimed to change that.
Quick Breakdown:
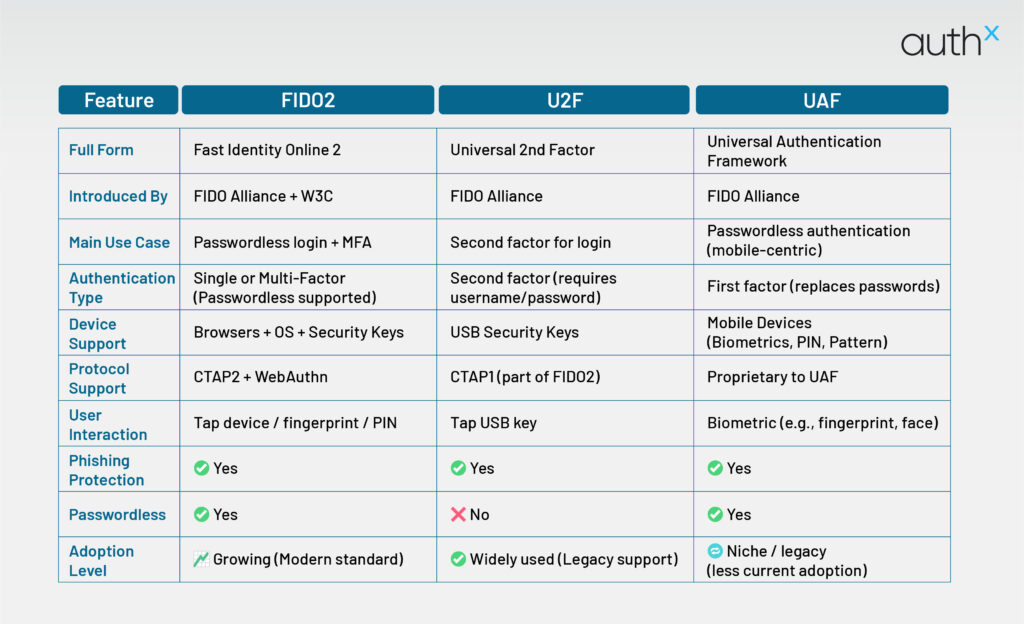
- FIDO U2F (Universal 2nd Factor):
A security key (like a YubiKey) is a second factor after entering your password. It’s strong, simple, and still in use today.
- FIDO UAF (Universal Authentication Framework):
This one’s more advanced—passwordless login using biometrics or PINs stored locally on your device. No password is required, but it only works within certain ecosystems (no browser-native support).
In a FIDO 1 vs FIDO2 comparison, FIDO was the blueprint. U2F and UAF were early drafts, but FIDO2 vs FIDO U2F shows how the new standard refines what came before.
FIDO2: Where Passwords Go to Die!
FIDO2 is the next generation. It takes everything good about U2F and UAF and adds what was missing. It’s cross-device, browser-native, and genuinely passwordless.
What makes it tick? Two key technologies:
- WebAuthn – This W3C standard is built right into browsers and platforms. It lets websites and apps communicate directly with your authentication device (like your phone, security key, or laptop).
- CTAP2 (Client to Authenticator Protocol) – This handle how the authenticators (your devices) interact with browsers. It allows roaming authenticators over USB, NFC, or Bluetooth.
It’s not just futuristic. It’s here now. Face ID on a MacBook logging you into your work portal? That’s FIDO2. A security key that replaces your password entirely? Also, FIDO2.
CTAP Decoded: CTAP1 vs. CTAP2
We get asked this a lot: “Is CTAP different from FIDO?” Think of CTAP1 as FIDO U2F reborn, it powers second-factor login via hardware keys.
CTAP2, however, powers FIDO2 vs OTP and FIDO2 vs U2F scenarios: it’s what enables passwordless and MFA solutions to work across platforms.
Here’s the quick cheat sheet:
| Spec | What It Means | Purpose |
|---|---|---|
| CTAP1 | FIDO U2F reborn | Second-factor login with hardware keys |
| CTAP2 | Backbone of FIDO2 | Passwordless + multi-factor auth |
One security lead we spoke with summed it up best:
“CTAP1 is like your old flip phone, it still works. CTAP2 is the smartphone running your life.”
Roaming vs. Platform Authenticators: Why You Need Both?
If you’ve ever tapped a YubiKey or used Face ID to log in, you’ve experienced both sides of the FIDO vs WebAuthn and U2F vs WebAuthn discussion.
- Roaming Authenticators: These are portable YubiKeys, with your phone acting as a passkey via NFC or Bluetooth. They are great for people who move between devices or share workstations (think nurses, field workers, contractors).
- Platform Authenticators: These live inside your device. Think Windows Hello, Face ID, or Touch ID. They’re fast and built into the hardware you’re already using.
In any FIDO2 vs FIDO U2F breakdown, flexibility wins. That’s why both are crucial.
How FIDO2 Works?
Let’s walk through the process, start to finish.
- Registration: When a user signs up or sets up a new device, it generates a key pair. The public key goes to the service (e.g., your SSO portal). The private key stays on the device, unshared and unphishable.
- Authentication: When the user logs in, the service sends a challenge. The device signs the challenge using the private key. That signed response is proof the user is who they say they are.
- Biometric or PIN Unlock: To unlock that private key, users may scan their faces, touch a fingerprint sensor, or enter a PIN. That check stays local, it never leaves the device.
It’s the most secure answer to the U2F vs FIDO2 and WebAuthn vs U2F questions: no shared secrets, no passwords, no phishing.

FIDO vs. FIDO2: The Cheat Sheet
| Feature | FIDO U2F (CTAP1) | FIDO UAF | FIDO2 (WebAuthn + CTAP2) |
|---|---|---|---|
| Auth Type | Second factor | Passwordless (device) | Passwordless, MFA, 2FA |
| Devices | Hardware keys | Phone or PC only | Keys, phones, biometrics |
| Web Integration | No | No | Yes (native browser support) |
| Still Relevant? | Yes (legacy use) | Niche | 100%—it’s the future |
Benefits of FIDO2
Why is FIDO2 vs OTP even a thing? Because OTP authentication still relies on secrets and network transmission. With FIDO2, you get:
- Built-in phishing resistance
FIDO2 stops phishing at the protocol level by eliminating the need to send credentials over the network. Even if a user clicks a malicious link, there’s no password to steal. That makes it a game-changer for social engineering defenses.
- Eliminates shared secrets
No more storing passwords or OTPs on the server. FIDO2 uses cryptographic key pairs, keeping the private key safely on the user’s device. This removes the risk of credential stuffing and data breaches from stolen secrets.
- Local biometric validation = better privacy
Biometric data never leaves the device—it’s used only to unlock the private key stored locally. That means organizations get strong assurance, and users keep control of their personal data. It’s a win-win for security and privacy compliance.
- Ready for HIPAA, NIS2, and more
FIDO2 aligns with modern regulations that demand strong authentication and minimal data exposure. It supports Zero Trust principles and passwordless mandates now appearing in healthcare, finance, and critical infrastructure. You’re not just future-proofing, you’re staying audit-ready.
- Lower helpdesk load—no more “reset password” days
When there are no passwords to forget, there’s nothing to reset. That means fewer support tickets, happier users, and IT teams that can focus on strategic work. FIDO2 reduces login friction while improving security posture.
Real-World Challenges
There are a few challenges before you go all in on passwordless authentication solutions.
- Legacy Systems: Not every app or browser is FIDO2-ready. You’ll need fallbacks or wrappers for older tools.
- User Onboarding: People don’t like change. You’ll need a smooth setup flow and a little handholding.
- Hardware Costs: Rolling out hardware keys at scale can add up. But compare that to the cost of a breach or repeated lockouts. It’s an easy ROI conversation.
- IAM Integration: Your identity stack needs to be FIDO2-aware. Make sure your SSO, MFA, and policy engines can handle it.
How AuthX Makes FIDO2 Work in the Real World?
We built AuthX with real-world challenges in mind. It supports WebAuthn, CTAP1, and CTAP2 right out of the box, so organizations don’t have to worry about compatibility. Whether you’re using platform authenticators like Face ID or roaming keys like YubiKey, AuthX integrates with both easily. It’s purpose-built for complex environments like healthcare, finance, manufacturing, and virtual desktop infrastructure (VDI), where security can’t come at the cost of usability.
AuthX also plays well with your existing identity stack, including IAM platforms, policies, and compliance frameworks. Most importantly, it’s designed to make secure login feel invisible. Users just log in, while the complexity stays behind the curtain.
Final Thoughts: Passwordless Is Inevitable. FIDO2 Just Got Us There.
The trend is no longer emerging; we are actively part of it. FIDO2 is already embedded in your devices, baked into your browsers, and supported by major platforms.
What’s left is adoption and making that adoption painless.
So, if you’re ready to ditch the password and the reset tickets that come with it, the next step is clear.
Explore how AuthX can help your team roll out FIDO2 authentication, without friction.
Want to see it in action?
Let’s talk. You’ll be surprised how quickly “passwordless” can go from buzzword to baseline
Frequently Asked Questions (FAQs)
What's the main difference between FIDO vs FIDO2?
FIDO is the original standard; FIDO2 is the evolution. While FIDO (like U2F) supported 2 factor authentication solutions(2FA), FIDO2 enables full passwordless login.
How does FIDO2 compare to older methods like TOTP?
In the FIDO2 vs OTP discussion, FIDO2 wins with phishing resistance, no shared secrets, and seamless biometric use.
Which is more secure: FIDO U2F vs FIDO2?
FIDO2. It supports both second factor and full passwordless flows, making it more flexible and secure than U2F alone.
Is there a use case for U2F vs FIDO2 in modern environments?
Yes, U2F is still used in legacy environments, but FIDO2 is recommended for futureproofing.
What about WebAuthn vs U2F, are they compatible?
WebAuthn supports U2F devices (thanks to CTAP1), but upgrading to FIDO2/WebAuthn gives you more features and browser-native support.


