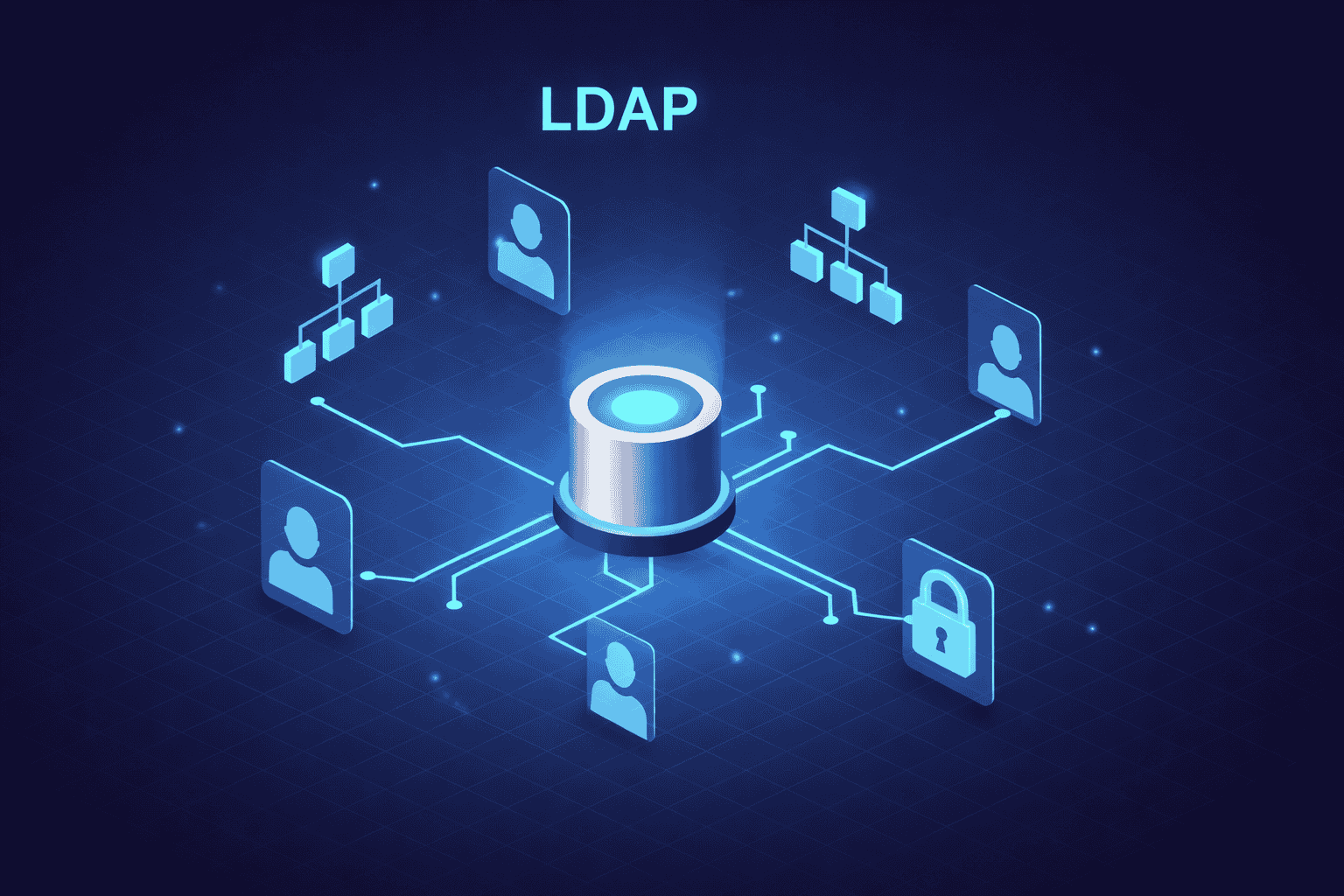
Understanding LDAP: Authentication, Components, and Common Uses
Long before today’s cloud-ready identity systems, organizations struggled with heavy, complex directory protocols that couldn’t keep up with the fast-growing


Long before today’s cloud-ready identity systems, organizations struggled with heavy, complex directory protocols that couldn’t keep up with the fast-growing

Do you know that, despite the rise of modern cloud protocols, roughly 5% of the global Identity & Access Management

Password managers and Single Sign-On (SSO) both make logging in easier, but they are different tools. Each lets you use

We like to say security is complicated because it makes us feel like we’re doing something impressive. But the truth is, the

Imagine it’s 9:00 AM on a Monday. An employee is ready to start the day, logs in once to their workstation. Instantly, the
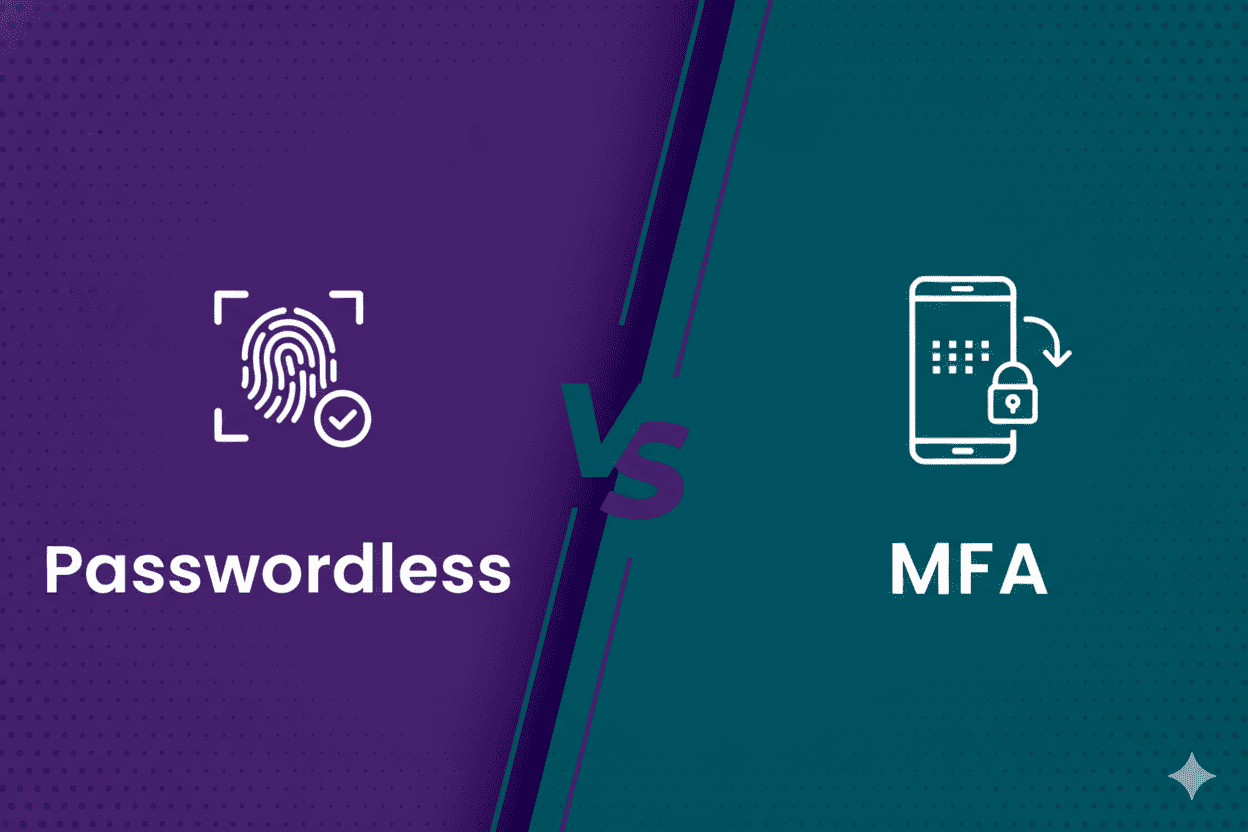
If a user denies an MFA request five times and then approves it on the sixth, that isn’t authentication. It’s just giving in. And that’s exactly what is happening across

Giving someone access to a system isn’t just flipping a switch. It’s opening a door. And like any open door,

Password spraying is one of the most insidious types of brute-force password attacks in cybersecurity today. Unlike traditional brute-force methods

In cybersecurity, understanding the difference between a Brute Force vs. Dictionary Attack is critical to building strong authentication defenses. While