What is PBAC – Policy Based Access Control?

Most access control systems weren’t built for the way modern businesses operate today. They’re too rigid, too static, and too unaware of real-world context. That’s where Policy Based Access Control (PBAC) comes in.
We hear a lot of buzz about access control strategies – Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and now, Policy-Based Access Control (PBAC). If you’re navigating the ever-evolving world of cybersecurity, it’s easy to get lost in the jargon. But here’s the thing: PBAC isn’t just another acronym to memorize. It’s a mindset shift, one that gives organizations dynamic control over who can access what and when.
In this blog post, we’ll break down what is PBAC, how it works, and why more teams are moving toward it as the future of access management.
What is Policy Based Access Control?
Policy Based Access Control (PBAC) is an approach that uses contextual policies to determine access rights. Rather than relying solely on fixed roles (like RBAC) or user attributes (like ABAC), PBAC applies logic-driven rules that consider multiple variables—user roles, attributes, time of day, device type, risk level, location, and more.
Think of it as setting rules like:
“Allow access to the financial system only if the user is in the finance department, using a company-issued device, and accessing from within the U.S. during business hours.”
This kind of policy-driven access control allows for nuanced decisions that reflect real-time conditions.
The beauty of PBAC is that it doesn’t lock you into rigid access schemes. It adapts in real time. When policies change, access decisions change automatically.
PBAC vs RBAC vs ABAC: What’s the Difference?
We hear a lot of IT leaders say, “We already have RBAC authentication—why do we need another model?” That’s fair. But the answer usually comes down to this: context.
Here’s how the three compare:
| Access Model | Decision Based On | Flexibility | Use Case |
|---|---|---|---|
| RBAC | User’s role | Low | Fixed access permissions |
| ABAC | Attributes (user, resource, environment) | Medium | Complex access scenarios |
| PBAC | Policies using multiple factors | High | Context-aware, dynamic access decisions |
RBAC is great for simplicity. ABAC improves flexibility with attributes. PBAC goes one step further by layering business logic into policies, bringing contextual awareness into every access decision.
Why are Organizations Moving to PBAC?
The IT stack is only getting more complex. More apps. More endpoints. More users. And more risk.
Here’s why policy driven access control is gaining traction:
1. Context is King
Cyber threats today don’t follow a schedule. And neither should access rules. PBAC allows you to define access in context, meaning access to sensitive systems can depend on the situation, not just the user.
Example: A doctor may access patient records during work hours from the hospital network, but not from their personal phone on vacation.
2. Zero Trust Alignment
PBAC fits right into the Zero Trust model: “Never trust, Always verify.” Instead of defaulting to trust based on roles or attributes, PBAC evaluates the entire context for every access request, every single time.
3. Reduced Overprovisioning
We commonly hear security teams say, “We don’t know who has access to what anymore.” That’s often the byproduct of overreliance on static RBAC models.
PBAC solves this by giving you precise control, so access isn’t overextended and can be revoked automatically when conditions change.
4. Regulatory Compliance Made Simpler
Whether it’s HIPAA, GDPR, or PCI DSS, compliance depends on tight access control. PBAC makes it easier to enforce fine-grained policies and maintain logs that prove compliance without rewriting your access rules every quarter.
Characteristics of PBAC
What makes PBAC unique? Here are some defining traits:
- Context-Aware Decisions: PBAC evaluates environmental, device, and behavioral data at the moment of the access request.
- Centralized Policy Management: Policies are centrally authored and updated, ensuring consistent enforcement across systems.
- Real-Time Enforcement: Access decisions are made in real time, based on up-to-date context and business rules.
- Scalability: Because policies are not hard coded into individual apps, PBAC can scale across complex, multi-cloud, hybrid environments.
- Flexibility: Supports conditional logic like time-based restrictions, risk-based controls, and dynamic approvals.
How Does Policy Based Access Control Work?
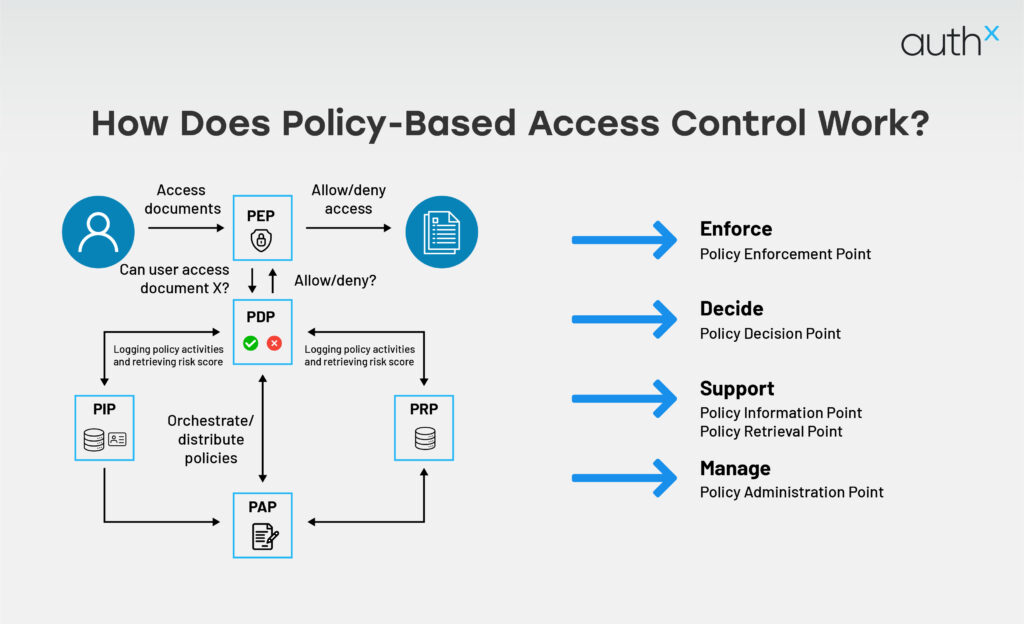
PBAC isn’t just about writing policies, it’s about how those policies are interpreted and enforced in real time. Here’s a behind-the-scenes look at how Policy-Based Access Control functions.
Policy Definition
This is where business logic is defined using if/then conditions. For example:
IF user.department = “Finance” AND user.location = “HQ” AND device.compliant = true THEN allow access to BudgetApp.
Policy Decision Point (PDP)
The PDP evaluates incoming access requests against defined policies. It acts as the brain of the system, making the access decision.
Policy Enforcement Point (PEP)
The PEP is the gatekeeper. It enforces the decision from the PDP by either granting or denying access at the application or resource layer.
Policy Administration Point (PAP)
The PAP is where admins create, update, and manage access policies. It provides a UI or API for defining rules, setting conditions, and mapping attributes.
Attributes
PBAC relies heavily on contextual attributes:
- User attributes: Department, clearance level, role
- Environmental attributes: Time, location, IP address
- Device attributes: Compliance status, OS version
- Risk attributes: Login behavior, threat intelligence
These attributes are evaluated in real time to determine access rights.
How does PBAC play out behind the scenes?
- A User Tries to Access a Resource
This could be a file, app, database, or dashboard.
- Access Request Sent to the PBAC Engine
The request contains metadata—user attributes, device, location, time, risk score.
- Policy Engine Evaluates the Request
It checks policies set by admins. For example:
IF user.department = “Finance” AND user.location = “HQ” AND device.compliant = true
THEN allow access to BudgetApp.
- Access Granted or Denied in Real-Time
The decision is logged, auditable, and reversible.
The key here is that policies are centrally managed, not buried in code or tucked into individual apps. That’s what makes policy based access management scalable.
Real-World Use Cases of PBAC
Healthcare
A nurse can view patient records only during their shift and only for patients in their care group. If they try to access it from a personal device or outside the hospital network, access is blocked.
Finance
Access to the trading platform is restricted based on:
- Job role (trader)
- Location (onsite office only)
- Time (market hours)
- Device compliance (corporate laptop)
This is a perfect example of an access control policy tailored for security and compliance
Higher Education
Professors can access grading systems during active semesters and only for courses they’re assigned to. Temporary access policies expire at semester end, no manual cleanup needed.
Advantages of PBAC
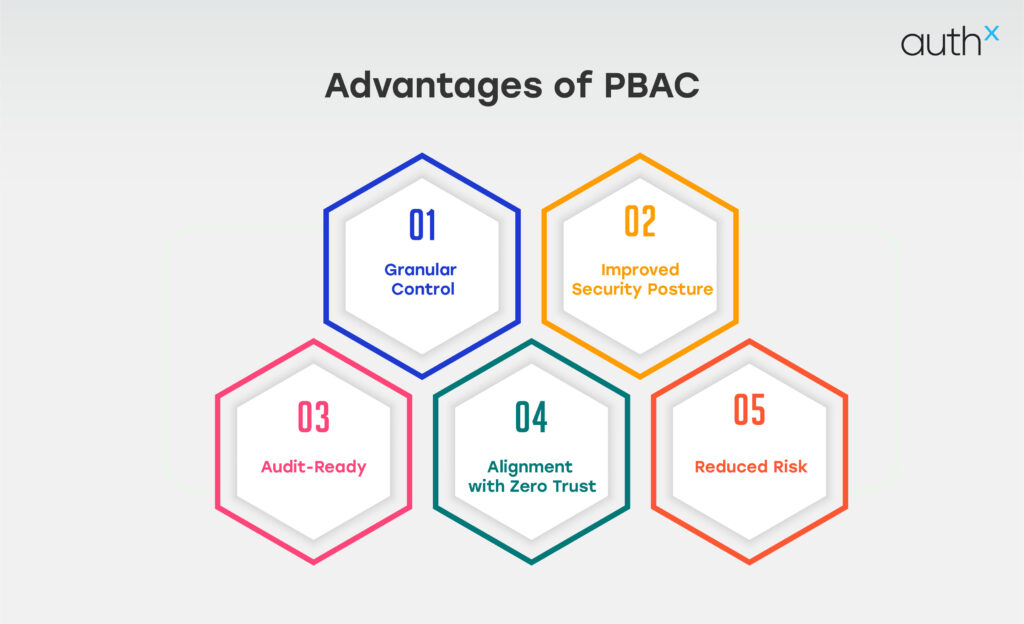
- Granular Control
Define highly specific access rules based on real business logic.
This means users get access only under the exact conditions you define—nothing more, nothing less.
- Improved Security Posture
Limit access to only what’s necessary, when and where it’s needed.
By shrinking the attack surface, PBAC helps prevent unauthorized or risky access in real time.
- Audit-Ready
Log every access decision, including context and policy used.
This makes it easier to prove compliance and investigate incidents without manual tracking.
- Alignment with Zero Trust
Dynamic evaluation replaces outdated static permissions.
Each request is verified in context, supporting “never trust, always verify” security principles.
- Reduced Risk
Minimize insider threats and lateral movement by limiting blanket permissions.
Fine-tuned policies ensure users can’t escalate privileges or access sensitive resources by default.
Challenges to Consider
No system is perfect. PBAC has its challenges:
- Policy Design Requires Thought: You’ll need to map real-world scenarios into clear, logical policies. It’s not always plug-and-play.
- Visibility and Testing: Bad policies can block critical access. You’ll need tools that let you simulate and test policies before rolling them out.
- Cultural Shift: If your team is used to RBAC, moving to PBAC may require a mindset change and cross-functional collaboration (security, IT, HR, compliance).
That said, the benefits often outweigh the complexity, especially in fast-moving, highly regulated environments.
How to Get Started with PBAC?
You don’t need to overhaul your entire access model overnight. Here’s a simple path forward:
- Audit Your Current Access Controls
Where are the gaps? Where is access too rigid or too loose?
- Identify High-Risk Areas
Start with systems where conditional access would add real value—like financial records, patient data, or dev environments.
- Define Sample Policies
Work with business stakeholders to create logical rules. Start small:
“Finance managers can only approve expenses >$10,000 during business hours from HQ.” That’s another solid example of an access control policy in action.
- Pilot and Iterate
Use Policy Based Access Control software that supports PBAC natively or integrates with your existing IAM solutions or SSO solutions.
- Educate and Align Your Teams
PBAC isn’t just an IT project. Get HR, legal, and compliance onboard early.
PBAC is Not a Trend, It’s a Necessary Upgrade
If you’re managing access with a role-based model that hasn’t evolved in years, it’s time to rethink. Policy based access management gives you the flexibility and control to handle today’s access complexity with policies that reflect real business logic.
Final Thoughts
What is PBAC access control? It’s not just another tech acronym, it’s a smarter way to think about who should have access and why.
By combining context, logic, and real-time decisions, Policy Based Access Control (PBAC) empowers security teams to enforce dynamic, risk-aware access without compromising usability.
And as businesses continue to scale across clouds, devices, and time zones, that kind of control isn’t just nice to have. It’s critical.
FAQs
What is PBAC in access control?
PBAC, or Policy Based Access Control, is a dynamic security model where access decisions are made based on real-time policies that factor in user role, context, device, and risk. It enables smarter, conditional access across systems.
Can you give an example of access control policy in PBAC?
A typical example of access control policy might state: “Marketing users can only access the campaign system during business hours from managed devices located within the U.S.”
How is policy driven access control different from RBAC?
While RBAC assigns permissions based solely on static roles, policy driven access control considers real-time conditions and user context, offering more granular and flexible security decisions.
Do I need special software for PBAC?
Yes. Implementing PBAC effectively often requires Policy Based Access Control software that can centralize policies, simulate outcomes, and integrate with IAM platforms for real-time enforcement.





