We’ve all been there: scrambling to remember the password we set months ago, trying to recover an account we’ve forgotten about, or worse, dealing with the endless cycle of resetting passwords because the “secure” ones are just too hard to remember. But what if we told you there’s a way to completely ditch this mess? No more passwords. No more forgotten credentials. That’s where token-based authentication comes in.
Why We Need a Better Solution?
Take a moment to think about how much time your team spends handling password-related issues. We recently spoke to a healthcare IT manager who shared that his team was wasting hours each week just managing password resets. “It’s a constant headache,” he said. “Our staff spends more time on passwords than actual work.” Sound familiar?
This isn’t just a healthcare issue, organizations everywhere are stuck in the same frustrating loop. Passwords are simply too risky and inefficient. But there’s a better solution: token-based authentication. Let us explore why this is the future of secure, passwordless solutions.
What is Token Based Authentication?
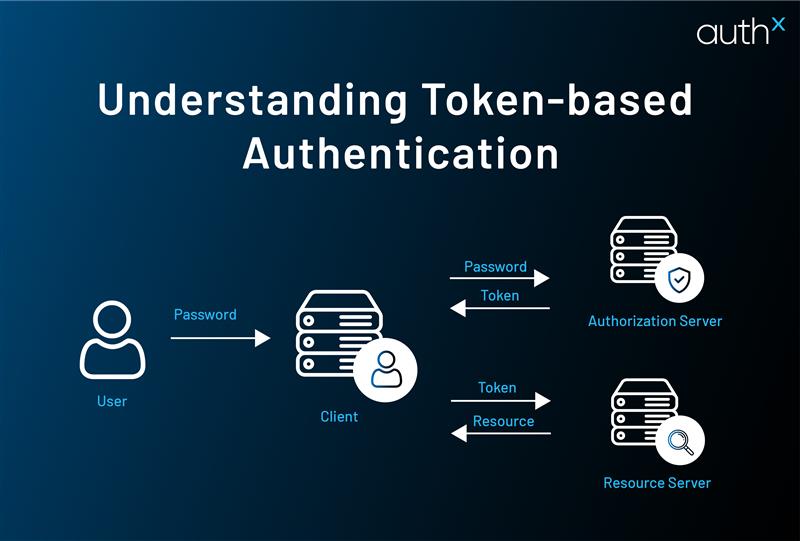
Token-based authentication works a little differently from the traditional password systems you’re used to. Instead of relying on a password to verify someone’s identity, a system issues an authentication token after the user logs in for the first time. This token acts as proof of identity and allows them to continue accessing the system, no passwords required.
Here’s how it works:
- Login – The user logs in with their credentials (like a username and password) once.
- Receive Token – After successful login, they’re issued an auth token.
- Authentication – The authentication token is used for subsequent requests, no need to re-enter a password.
- Expiration – Tokens are time-sensitive and expire after a set period.
The beauty of this system? It reduces the chances of an account being compromised and removes the headache of remembering (and resetting) passwords.
What is Token in Token Authentication?
We’ve been throwing around the word “token”, so let’s clarify: what is token exactly?
A token is a digital credential that proves your identity to a system. Unlike passwords, they’re temporary, encrypted, and hard to steal. And when we say what is token authentication, we mean a process where a system relies on authentication tokens instead of passwords to validate user identity.
To put it simply:
- What is token? It’s your digital key.
- What is token authentication? It’s how systems trust that key instead of asking you for a password.
- And when done right, what is token based authentication? It’s the secure, future-proof method of making all this happen invisibly and seamlessly.
Understanding Authentication Token Types & Uses
| Token Type | Purpose | Used In | Pros | Cons |
|---|---|---|---|---|
| Hardware Token | Generates one-time codes | MFA, banking, enterprise logins | Very secure, works offline | Expensive, not user-friendly to carry |
| Software Token (TOTP) | App-based time-based codes | 2FA for apps and websites | Free, widely supported | Phishable, tied to one device |
| JWT (JSON Web Token) | Encodes user/session data securely | APIs, SSO, OAuth | Stateless, portable, fast | Needs strong signing/validation |
| Bearer Token | Grants access without repeated login | REST APIs, microservices | Easy to use and implement | If leaked, can be reused by attackers |
| Biometric Token | Authenticates via biometric data | Mobile apps, healthcare, enterprise | Fast, convenient, hard to fake | Device-specific, privacy concerns |
| Email/SMS OTP | Sends code to user via email or SMS | 2FA, account recovery | Simple to deploy, no app needed | Vulnerable to phishing and SIM swap attacks |
| OAuth Access Token | Delegates access to third-party resources | "Login with Google", mobile/web apps | Scalable, standardized | Short-lived, requires refresh token |
| FIDO2/WebAuthn Token | Enables phishing-resistant passwordless auth | IAM systems, Zero Trust environments | Strongest security, no shared secrets | Requires hardware or biometric support |
| Refresh Token | Issues new access tokens without login | OAuth2 flows, long-lived sessions | Enhances UX, maintains session continuity | Must be securely stored, long lifespan risk |
| ID Token | Verifies user identity after login | OpenID Connect, SSO flows | Contains user info for session context | Not intended for resource access |
Understanding the Types of Tokens

Let’s break down the key types of token based authentication used in modern systems:
- Access Token – A short-lived security token used to access APIs or services.
- Refresh Token – Used to obtain a new access token after the original expires, without re-authenticating.
- ID Token – Carries information about the user, like their identity, issued alongside the access token.
These different types of tokens each play a role in improving security and efficiency. Knowing the types of token-based authentication helps in implementing the right mix for your organization.
Why Token-Based Authentication is More Secure Than Passwords?
“Why is token-based authentication any more secure than passwords?” is probably what you’re asking yourself now. A password is just a collection of characters, after all. To put it clearly, tokens are significantly more complicated and challenging to hack than conventional passwords.
Here’s why:
- Encrypted Tokens – The auth token is an encrypted string of data that’s harder to intercept and use than a regular password.
- Limited Lifespan – Authentication tokens expire quickly, which means even if they’re intercepted, they’re only useful for a short time.
- No Password Storage – Authorization tokens aren’t stored in the same way passwords are, making them harder to steal through traditional methods.
How Tokens Fit into the Bigger Security Picture?
When paired with additional security mechanisms, such as Multi-Factor Authentication software, token-based authentication becomes even more effective. MFA provides a second layer of security, guaranteeing that even if an auth token is hacked, access is still denied without the second factor.
- Tokens + MFA – The two work seamlessly together to create an even stronger security net.
- Reduce Risks of Phishing – Since security tokens can’t easily be intercepted by traditional phishing methods, they offer additional protection.
Tap, Plug, Authenticate: Hardware Tokens Explained
We often think of authentication tokens as something floating around in the cloud – invisible, encrypted, and digital. But not all tokens live in software. Some are very real and fit in the palm of your hand.
These are called hardware tokens. These are physical devices like USB keys or smart cards, that carry a secure authentication credential. When plugged in or tapped, they prove your identity without requiring a password. Let’s break down the types:
- Connected tokens need to be physically inserted into a device — think USB keys like YubiKeys. When you plug one in, it verifies your identity automatically.
- Disconnected tokens generate one-time passcodes but don’t plug into anything, they’re usually standalone devices or even smartphone apps acting as digital versions.
- Contactless tokens are tap & go. They work wirelessly, often through NFC or Bluetooth, and are popular in healthcare and high-security environments.
Why do they still matter? Because hardware tokens offer an extra layer of protection, especially in environments where phishing risks are high and password fatigue is real. They’re tamper-resistant, difficult to clone, and perfect for industries that need strong, reliable 2FA or MFA.
We’ve seen organizations pair hardware tokens with cloud-based auth systems to create a hybrid approach: fast, secure, and frictionless access that works anywhere, whether you’re in the office or on the move.
Making Life Easier for Users
Users hate passwords—and we get it. They’re inconvenient, easy to forget, and constant sources of frustration. Fortunately, we’re getting closer to a world where users don’t have to think twice about logging in, thanks to token-based authentication. With authorization tokens, there’s no need to remember or enter passwords after the initial sign-in. Single Sign-On solutions allow users to access multiple systems without logging in again, and the entire experience becomes fast and frictionless. A key benefit of authorization tokens is that they remove the barrier between the user and the system.
The Risks and How to Mitigate Tokens
Of course, no security measure is perfect. The primary risk with authentication tokens is that they can be stolen, especially if transmitted over an unsecured connection. Here’s how to reduce that risk:
- Always Use HTTPS – Never transmit a security token over unsecured channels.
- Short Expiry Times – Set authorization tokens to expire quickly.
- Monitor Token Usage – Watch for unusual activity and revoke tokens if necessary.
Why You Should Adopt Token-Based Authentication?
Token-based authentication is more than a security upgrade, it’s a smarter, faster way to manage access. As organizations shift to the cloud and embrace Zero Trust, authentication tokens offer secure, passwordless access that users love, and IT teams can trust.
With AuthX, encrypted, temporary tokens replace passwords entirely eliminating resets, reducing risk, and simplifying access across systems. From healthcare to finance, organizations are turning to AuthX to future-proof their authentication strategy.
Ready to ditch passwords for good? Let’s talk about how token-based authentication with AuthX can work for your organization.


